This guide compares the most popular edge security solutions and offers recommendations for choosing the right vendor for your use case.
SD-Branch
Applications of Edge Computing
This blog discusses some of the applications of edge computing for industries like finance, retail, and manufacturing and provides advice on how to get started.
Edge Computing Examples
This blog highlights 7 edge computing examples from across many different industries and provides tips and best practices for each use case.
Edge Computing vs Cloud Computing
This guide compares edge computing vs cloud computing to help organizations choose the right deployment model for their use case.
Edge Computing Architecture Guide
This edge computing architecture guide provides information and resources needed to ensure a streamlined, resilient, and cost-effective deployment.
NIS2 Compliance & Requirements
This guide describes the 10 minimum cybersecurity requirements mandated by NIS2 and provides tips to simplify NIS2 compliance.
DORA Compliance & Requirements
This guide outlines the technical requirements for DORA compliance and provides tips and best practices to streamline implementation.
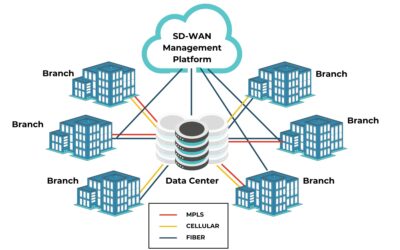
SD-WAN Management Guide
This SD-WAN management guide explains how this technology works, the potential benefits of using it, and the best practices to help you get the most out of your SD-WAN deployment.
Cisco 2900 EOL: Replacement Options
In this guide, we’ll compare migration options for the Cisco ISR 2900 EOL models to help you select a solution that suits your business use case, deployment size, and future growth.
Building an IoT Device Management System
An IoT device management system is meant to simplify and streamline the management of remote, hard-to-reach, and complex IoT devices and infrastructure.