This blog describes six potential edge computing use cases in healthcare that take advantage of the speed and security of an edge computing architecture.
Vendor Neutral Platform
Benefits of Edge Computing
This blog discusses the five biggest benefits of edge computing, providing examples and additional resources for companies beginning their edge journey.
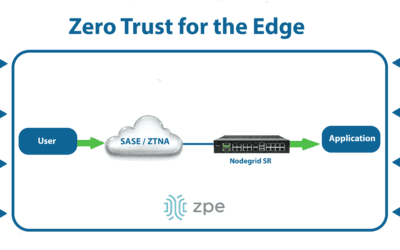
Improving Your Zero Trust Security Posture
This blog provides advice for improving your zero trust security posture with a multi-layered strategy that mitigates weaknesses for complete coverage.
Comparing Edge Security Solutions
This guide compares the most popular edge security solutions and offers recommendations for choosing the right vendor for your use case.
Applications of Edge Computing
This blog discusses some of the applications of edge computing for industries like finance, retail, and manufacturing and provides advice on how to get started.
Edge Computing Examples
This blog highlights 7 edge computing examples from across many different industries and provides tips and best practices for each use case.
Edge Computing vs Cloud Computing
This guide compares edge computing vs cloud computing to help organizations choose the right deployment model for their use case.
Edge Computing Architecture Guide
This edge computing architecture guide provides information and resources needed to ensure a streamlined, resilient, and cost-effective deployment.
Critical Entities Resilience Directive
With limited time to demonstrate compliance with the Critical Entities Resilience Directive, organizations should begin preparing now.
NIS2 Compliance & Requirements
This guide describes the 10 minimum cybersecurity requirements mandated by NIS2 and provides tips to simplify NIS2 compliance.